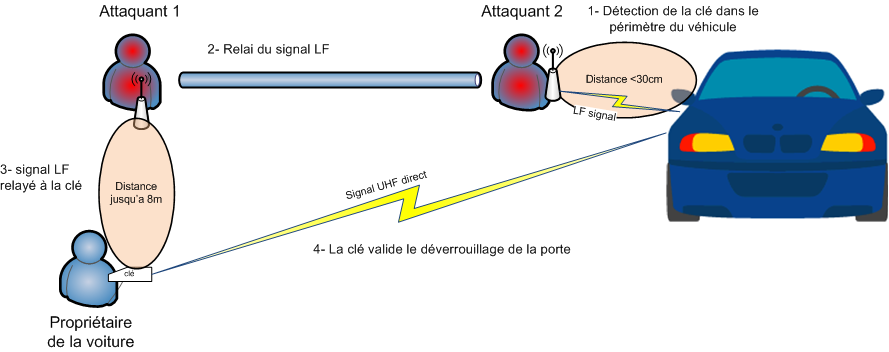
The relay attack in practice: (a) opening the door with the relay. (b)... | Download Scientific Diagram

A Defense Mechanism Against Replay Attack in Remote Keyless Entry Systems Using Timestamping and XOR Logic | Semantic Scholar
Defend Your Vehicle Against Relay Attack -Defense Technology Against Latest Automotive Theft Technique-

Car-Theft “Mystery Device”: Guarding against a Potential Problem, Real or Imagined – Feature – Car and Driver





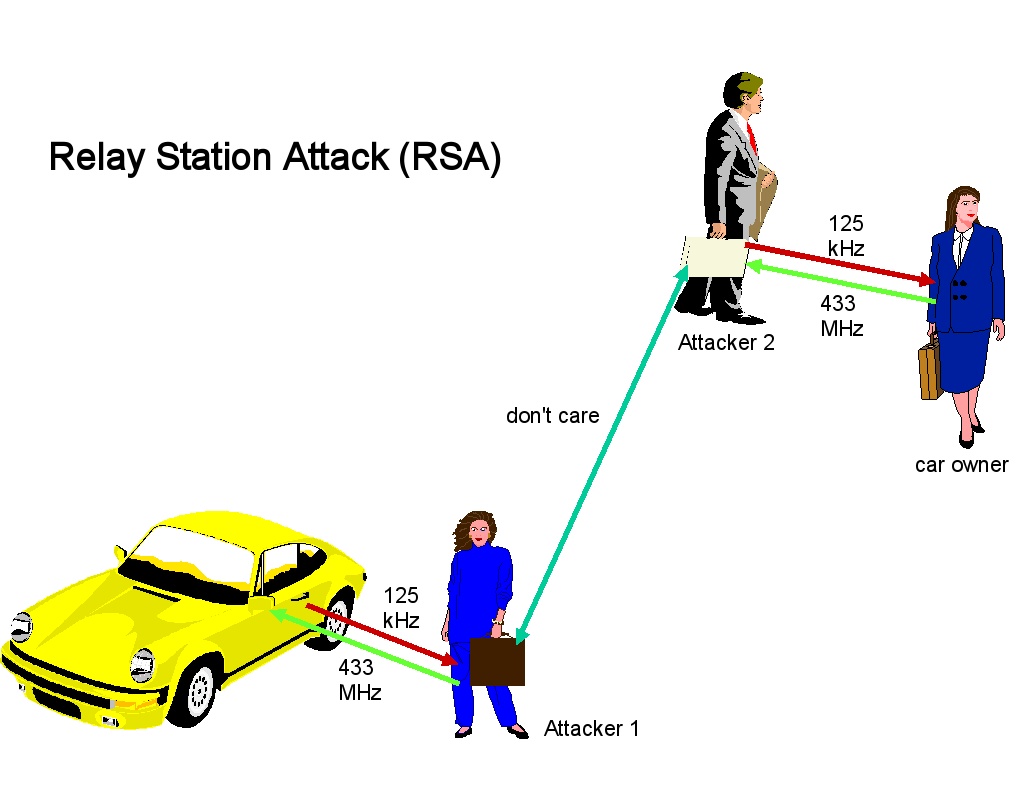



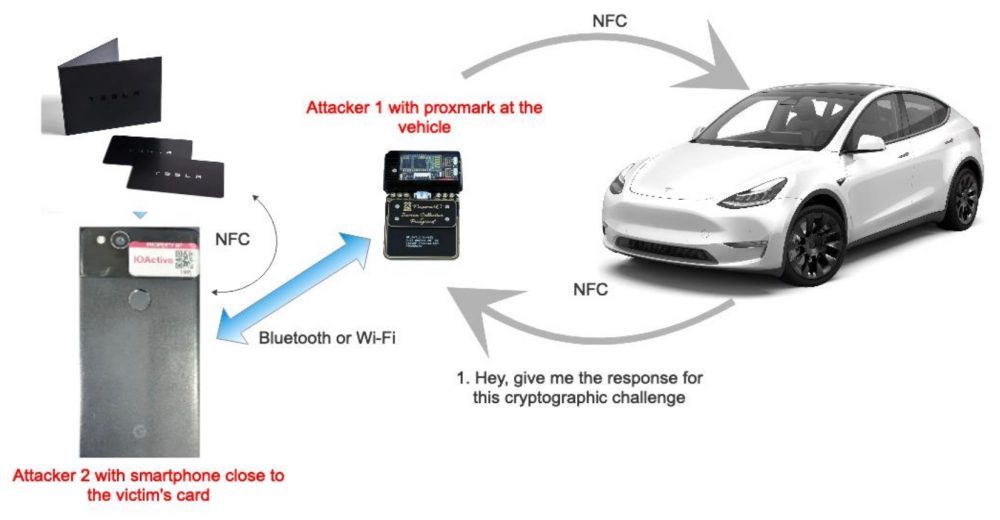

![[Video] Hackers Steal Tesla Model S using a Relay Attack [Video] Hackers Steal Tesla Model S using a Relay Attack](https://blog.drhack.net/wp-content/uploads/2018/10/Passive-Entry-Relay-Attack-Tesla-1200x720.jpg)